Welcome to the blog of Dr. Ken Tindell, CTO of Canis Automotive Labs. This blog is focused on the work
Canis is doing on CAN bus and CAN security, but also covers the design of
embedded software and hardware for automotive systems and the Yes We Can project at Canis that
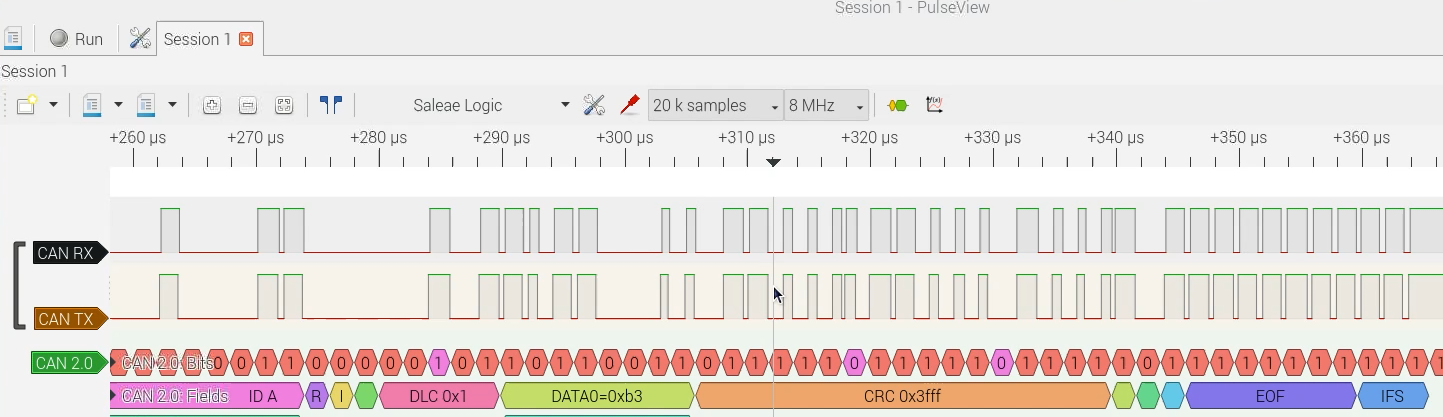
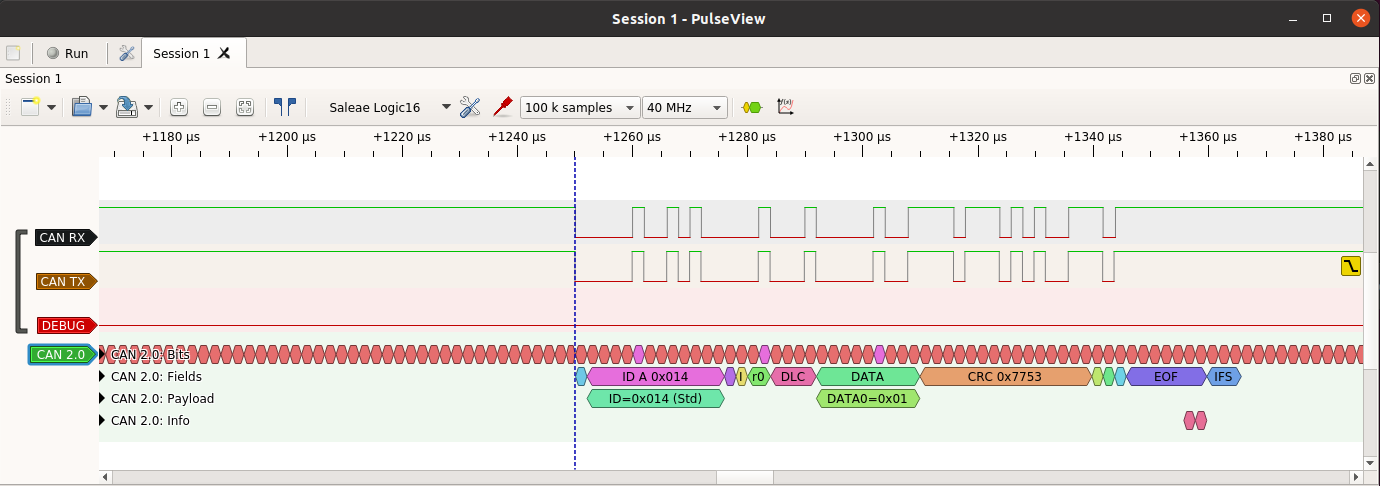
develops hardware, software and tools for CAN bus: the CANHack toolkit
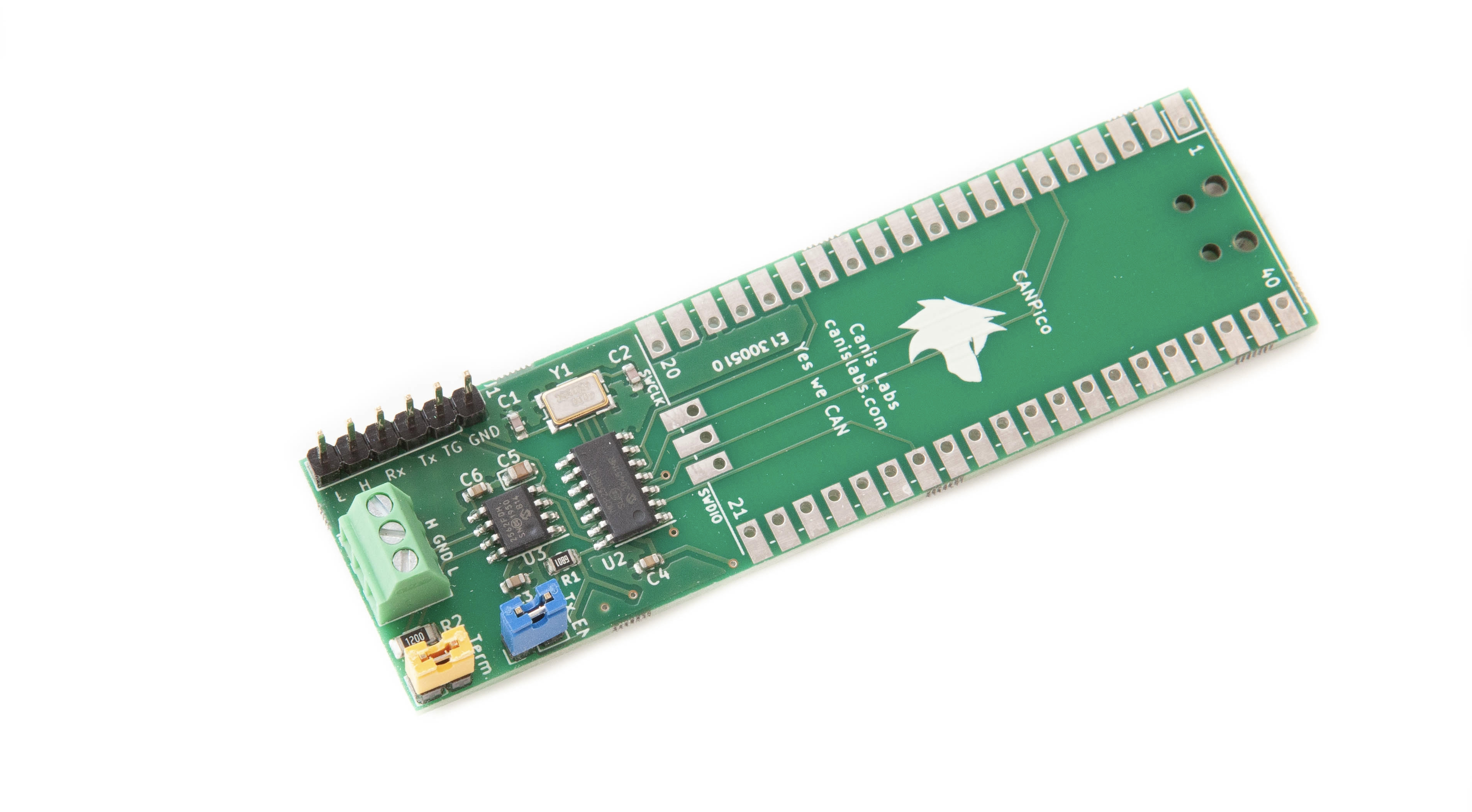
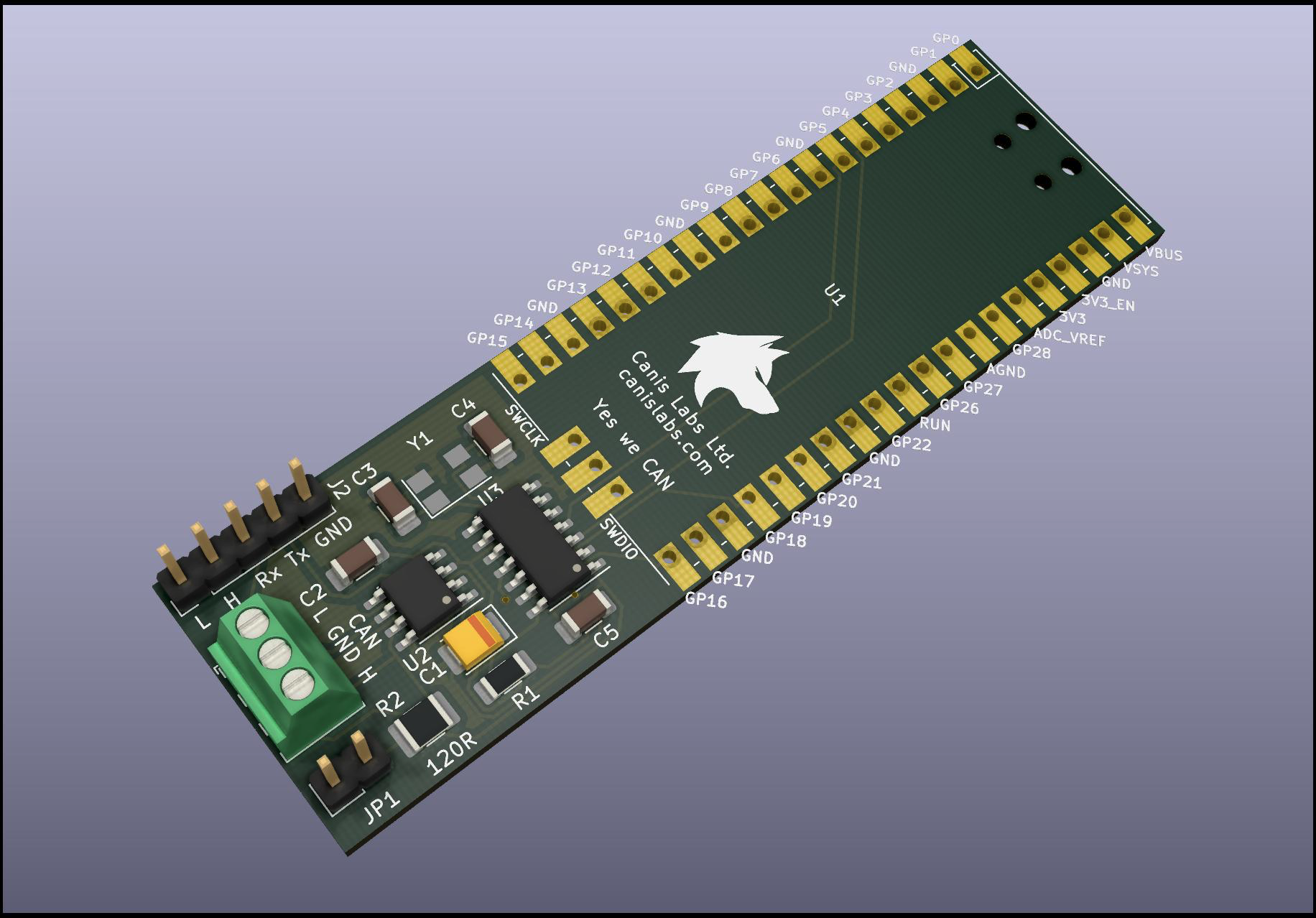
for injecting faults into the CAN protocol, CANPico and CANHack hardware boards for
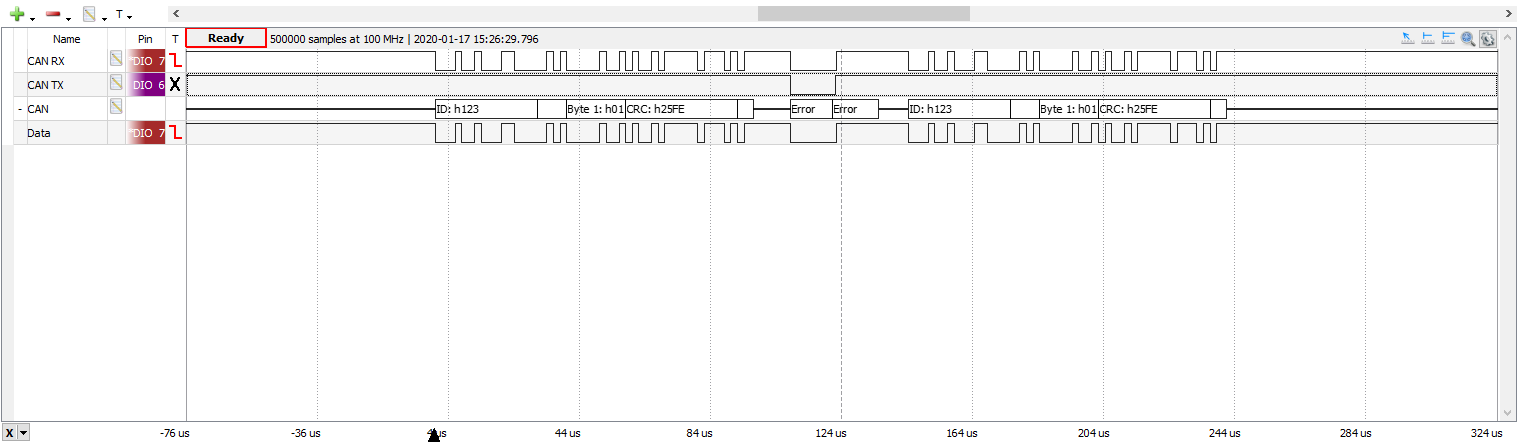
the Raspberry Pi Pico, and the can2
logic analyzer CAN protocol decoder.
Archive of posts with category 'CANHack'
CAN bus is a wildly successful fieldbus protocol that is perfectly designed for vehicle applications (even including spacecraft that have gone to Mars). But that success in handling sensors and...
I recently gave a 45 minute webinar at the ASRG on the topic of CAN protocol attacks, demonstrating five different attacks on the CAN protocol itself. There is also a...
The Janus Attack is a low-level CAN protocol attack where a single CAN frame contains two different payloads, so that a targeted device sees a different payload to other devices....
The CANPico board is at last available, and ready for order online from SK Pang. It’s been a long time coming, longer than we expected thanks to some major problems...
We have recently been developing an API for CAN under MicroPython for the new CANPico board from Canis Automotive Labs. There are some really neat features of the CAN support...
Canis Automotive Labs has three CAN boards in the pipeline and with luck we should be announcing availability in a few weeks, so we’ve produced a sneak preview of those...
The Raspberry Pi Pico doesn’t have a CAN controller built-in but that’s
no barrier: we can send CAN frames in software!
The CANHack toolkit includes support for various kinds of attacks on the CAN protocol, including three new unpublished attacks. These new hacks are described in this blog post. There is...
For the last few weeks we’ve been developing the CANHack toolkit for CAN protocol hacking. It’s a portable bit-banging library to emulate the minimal parts of the CAN protocol required...