Welcome to the blog of Dr. Ken Tindell, CTO of Canis Automotive Labs. This blog is focused on the work
Canis is doing on CAN bus and CAN security, but also covers the design of
embedded software and hardware for automotive systems and the Yes We Can project at Canis that
develops hardware, software and tools for CAN bus: the CANHack toolkit
for injecting faults into the CAN protocol, CANPico and CANHack hardware boards for
the Raspberry Pi Pico, and the can2
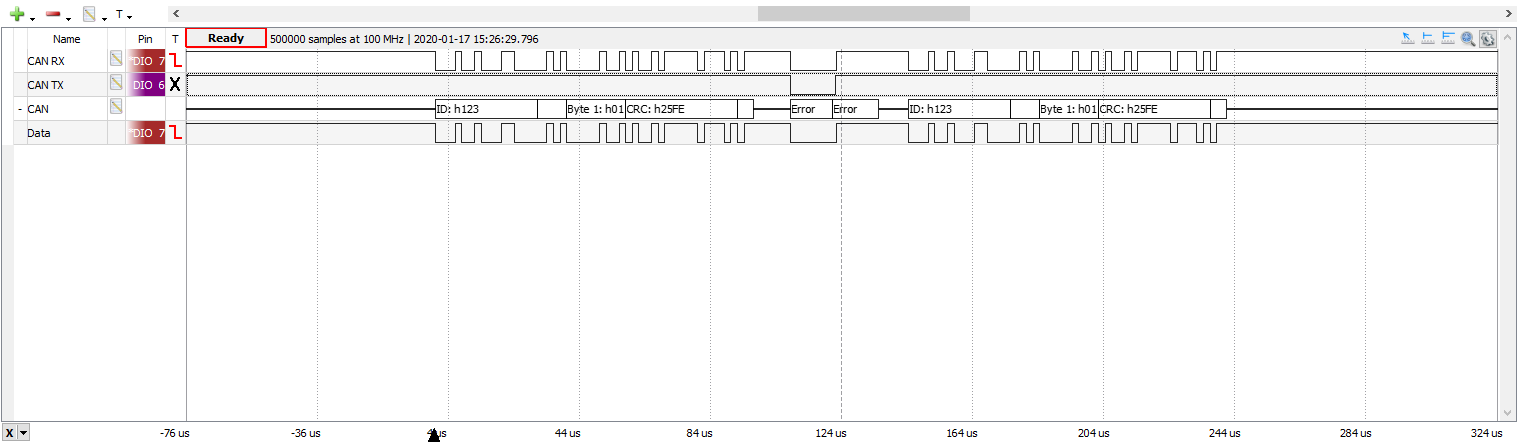
logic analyzer CAN protocol decoder.
Archive of posts with category 'CAN security'
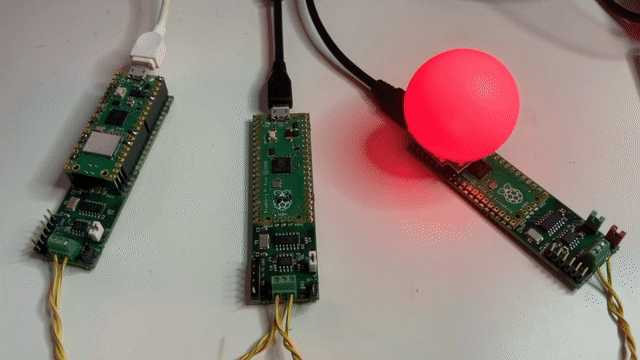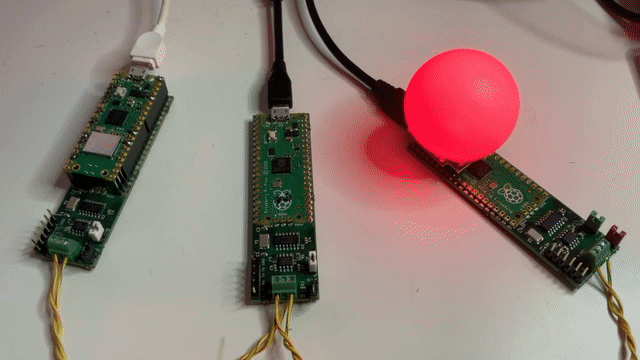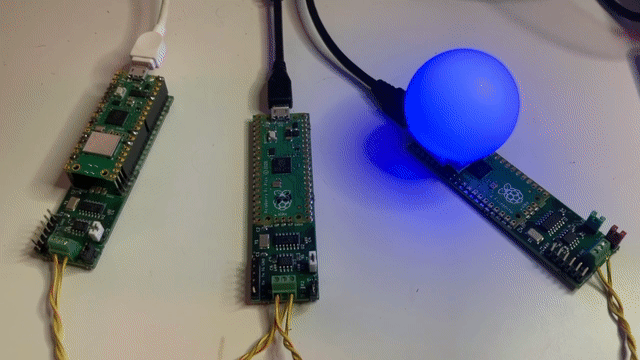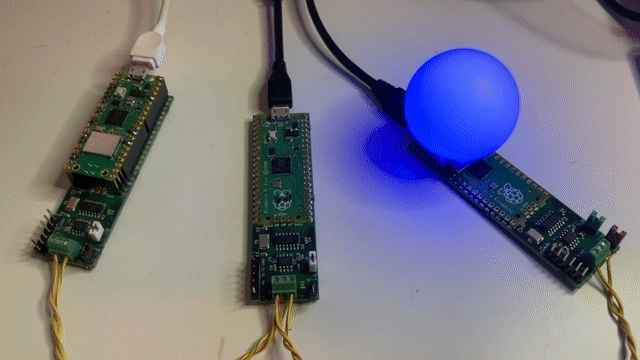
At first glance, an innocent little project for the Festive Season - Cheerlights on a Pico. Big Deal?!
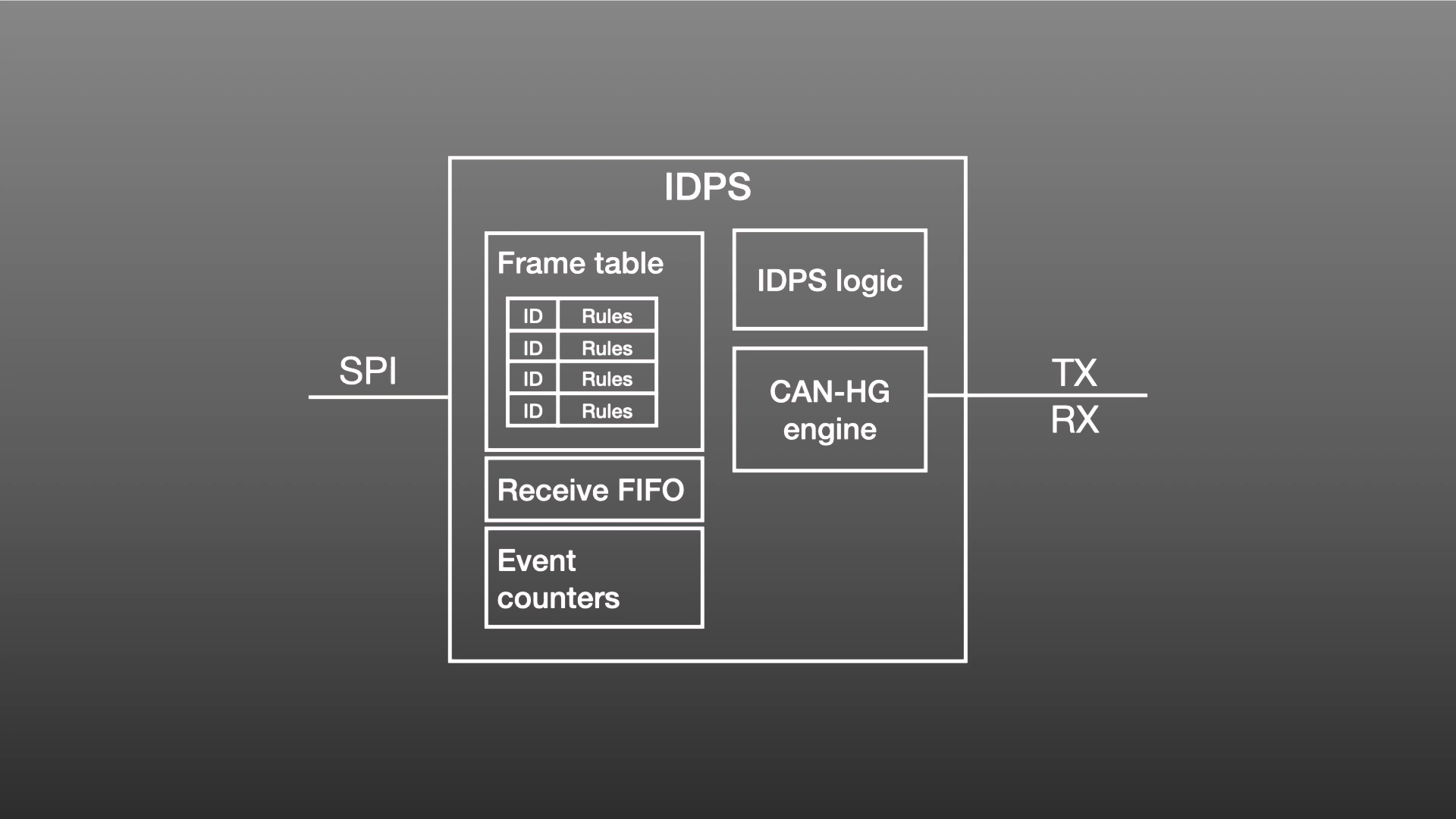
Episode 3 of this Defending CAN series discussed security gateways. This fourth episode describes hardware protection of CAN using the new CAN-HG augmentation of the CAN protocol. The episode describes...
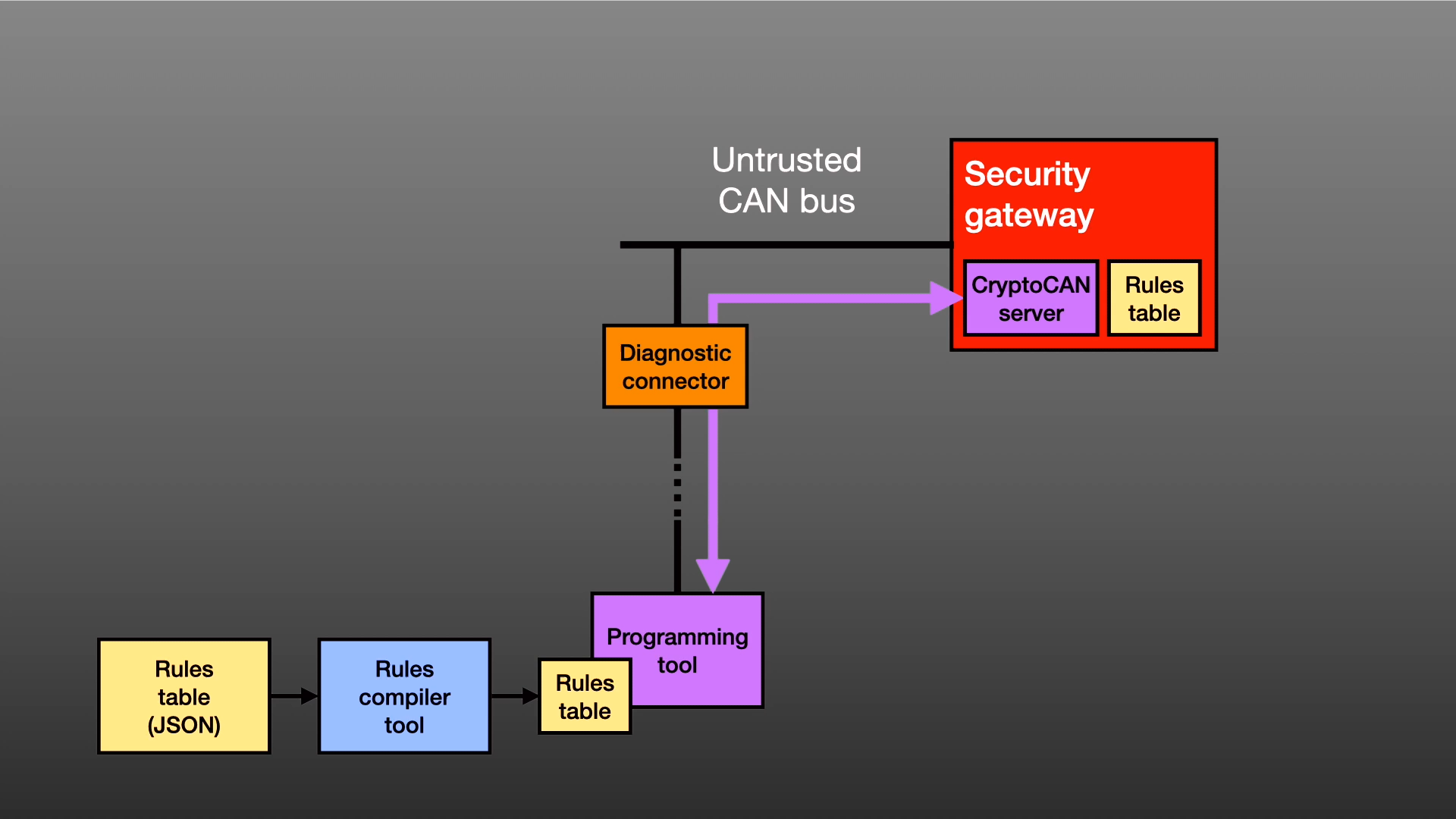
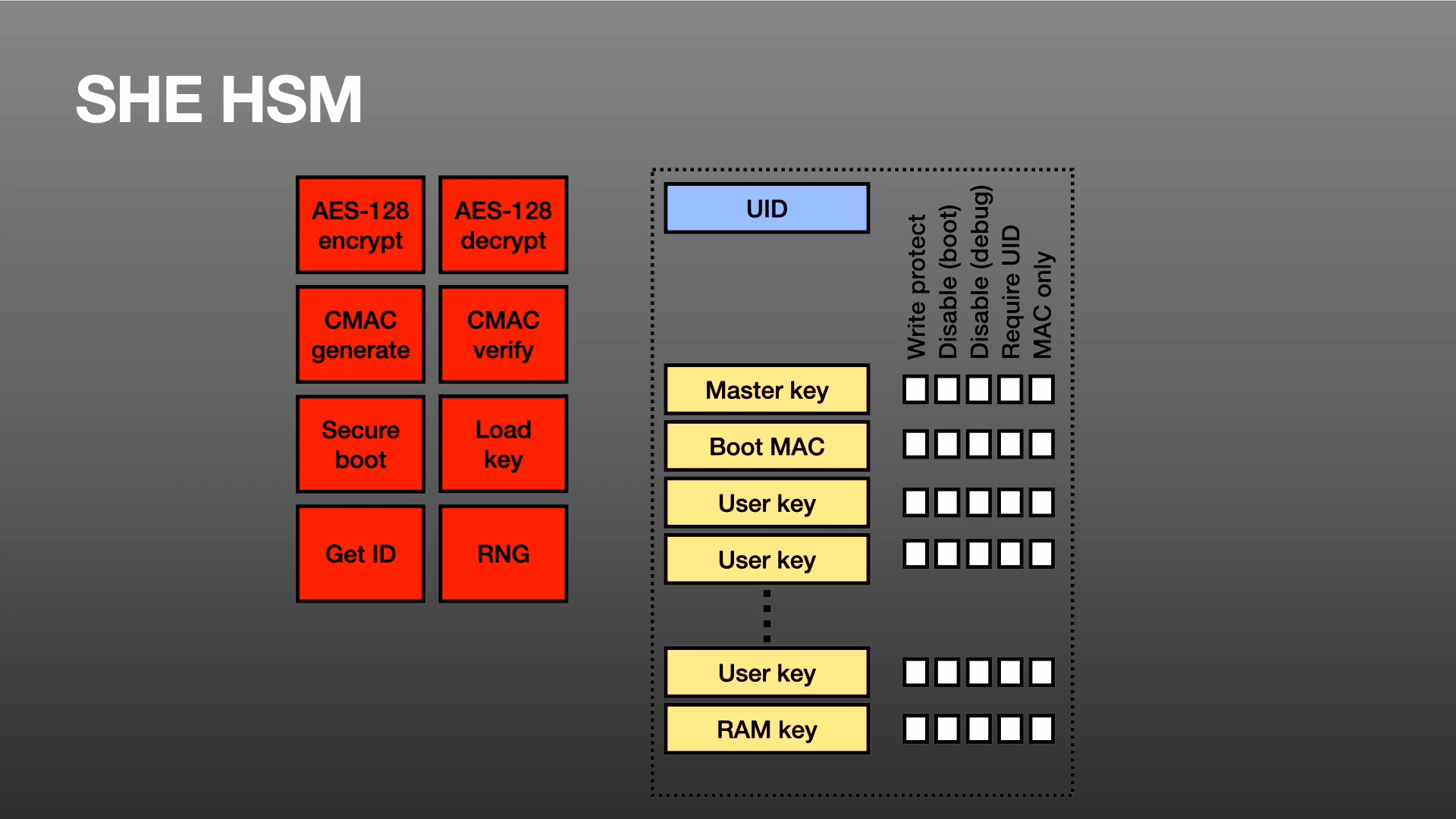
Episode 2 of this series covered cryptography on CAN. This third episode describes security gateways, using as a case study the Canis Labs security gateway. Covered are the things that...
Each episode in the series covers one technique for defending the CAN bus.
Episode 1 introduced CAN attacks
and talked about intrusion detection, the CCTV of CAN bus.
CAN bus is a wildly successful fieldbus protocol that is perfectly designed for vehicle applications (even including spacecraft that have gone to Mars). But that success in handling sensors and...
We said in our previous blog post that “Our next goal is to create a GTKWave filter so that an arbitrary waveform can be decoded” and in an early Christmas...
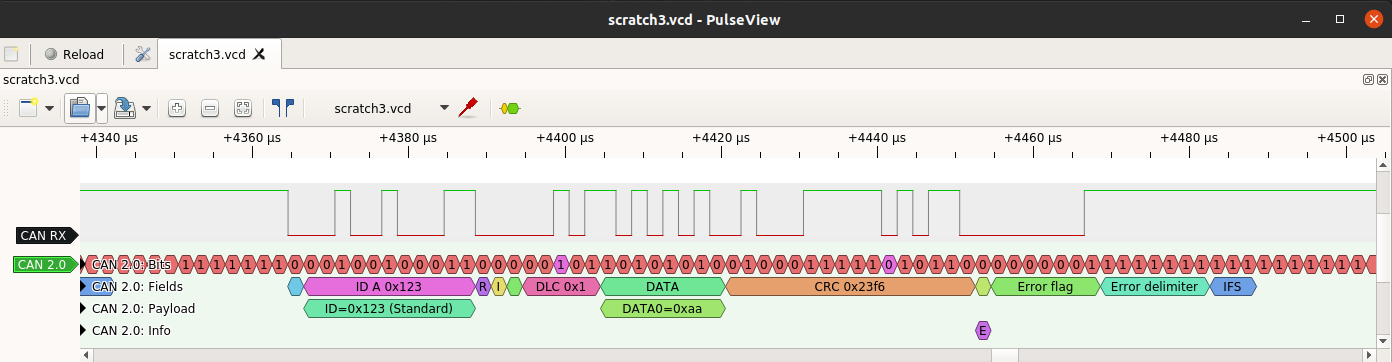
The CANHack toolkit includes support for various kinds of attacks on the CAN protocol, including three new unpublished attacks. These new hacks are described in this blog post. There is...
For the last few weeks we’ve been developing the CANHack toolkit for CAN protocol hacking. It’s a portable bit-banging library to emulate the minimal parts of the CAN protocol required...